Cyber-attacks threaten the reliability of business operations such as energy, production, supply chain, etc. and pose a significant risk to every company’s core business. The widespread adoption of digital technologies has helped companies increase efficiency and sustainability and reduce costs. Yet, increased connectivity makes it increasingly likely that companies are exposed to cyber-attacks on their […]
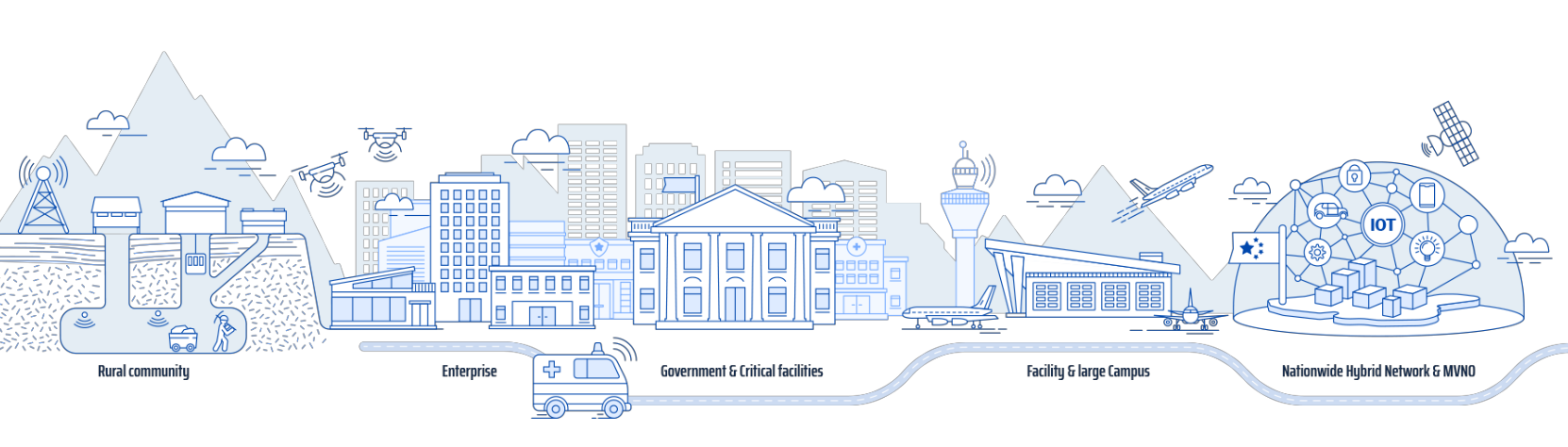
If data security and resilience is a priority in your cellular communications, it’s time to transform your private mobile network. We provide you with a fully controllable on-premises cellular environment that supports up to 10,000 users in both static and mobile field conditions, communicating locally and connecting worldwide. By routing all cellular traffic to your […]
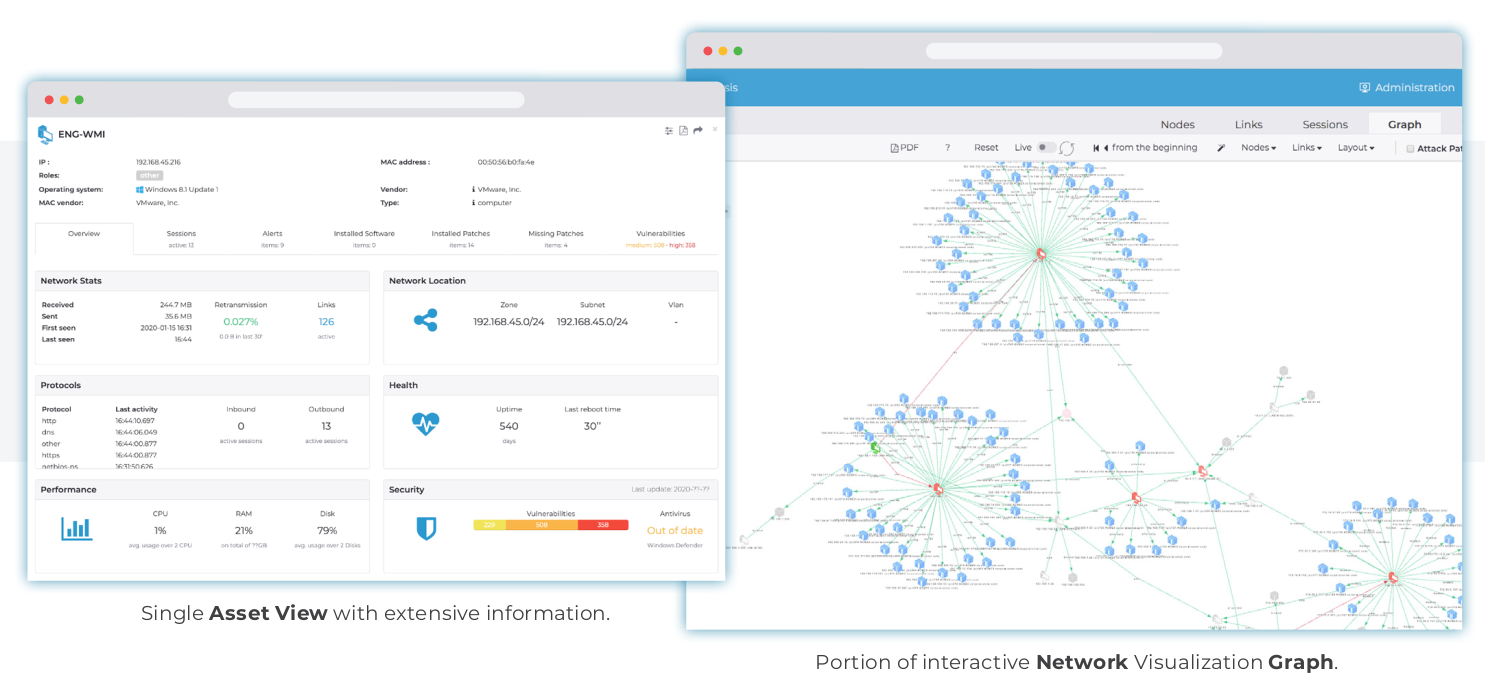
Better asset inventories and rapid threat detection should be sufficient justification for industrial companies to invest in continuous OT network monitoring. But product assessments should also consider future developments such as IT/OT cybersecurity convergence, external security support and digital transformation. Continuous operational technology (OT) network monitoring has become an essential part of every industrial/OT cybersecurity […]
Our partner Nozomi Networks, one of the leading companies in the field of OT and IoT Cyber Security, has released a free trial version of its core product Guardian for new users and to meet the visibility needs in OT networks. Thanks to this trial version, you will have real-time visibility into your existing operational […]
The Data Gap: IIoT and data analytics Today, companies, especially in the manufacturing sector, have advanced operational (OT) and information technology (IT) infrastructures. These technologies are so intertwined with the business processes of companies that they have become a part of the daily lives of the personnel using them. As these systems have evolved over […]
Welcome to the Internet of Things (IoT) revolution, a time when intelligence will be embedded everywhere, and synthetic devices and systems will increasingly make decisions. In this era of IoT, there will be billions of devices communicating with each other: analyzing, interacting, measuring, responding and initiating it all without any human input. To see how […]
Critical infrastructure cybersecurity has never been more important or challenging. These organizations have become prime targets for cybercriminals and hostile state actors. At the same time, digital transformation is expanding the attack surface with new devices and external connectivity. While most critical infrastructure facilities have invested in some cybersecurity defenses, many lack the resources needed […]