The notion that IoT devices are secure by design and/or that security features are enabled by default is deceptive, auditing and controls must match the fundamental challenges of IoT security today to be prepared for zero-day attacks. IoT projects promise unparalleled ROI for monitoring, diagnostics and analytics, enabling new business models. However, these projects lack […]
The concept of Digital Transformation is based on 3 pillars; High Processing Power (xPU Power) High volume storage Power (Storage) High speed communication power (Communications) All 3 technological foundations are related to the data generated/processed. In the coming Industry x.0 era, all industries will be based on data and its analysis. In order to get […]
In a rapidly changing world, the question is no longer whether you need to transform, but how. This change may differ for each organization and each business area. High connectivity, increased processing power and the ability to store high volumes of high-speed data appear to be the key elements in making Digital Transformation happen. But […]
Broad, Integrated and Automated Security with Real-Time Cybersecurity and Visibility for Industrial Control Networks As the backbone of critical infrastructure, industrial control systems (ICS) are found in all industries, including energy, power, water, manufacturing and even military applications. Over the last decade, ECS has become more automated and advanced, but also more connected to traditional […]
WHAT IS THE MITRE ATT&CK FRAMEWORK FOR EX/OT SECURITY? The MITRE ATT&CK framework threat modeling for Industrial Control Systems (ICS) classifies malicious cybersecurity incidents based on their operational technology (OT) environment. This framework design classifies each incident as a specific tactic and maps each tactic to one or more high-level technical categories. In essence, this […]
Cyberattacks can cause catastrophic business disruptions and lead to financial losses reaching hundreds of millions of dollars. The World Economic Forum’s 2020 Global Risk Report ranked cyberattacks on critical infrastructure that disrupt operations and disrupt operations among the top five emerging global risks. Accenture also estimates in its research that the number of cyber attacks […]
When Florida law enforcement announced a cyberattack in the Oldsmar water district, we were startled to learn that cyberattacks can actually reach inside our homes, right down to the water we drink and use. It was alarming to learn that a cyber attacker had leveraged the TeamViewer app to remotely access the city’s water treatment […]
Cyber-attacks threaten the reliability of business operations such as energy, production, supply chain, etc. and pose a significant risk to every company’s core business. The widespread adoption of digital technologies has helped companies increase efficiency and sustainability and reduce costs. Yet, increased connectivity makes it increasingly likely that companies are exposed to cyber-attacks on their […]
If data security and resilience is a priority in your cellular communications, it’s time to transform your private mobile network. We provide you with a fully controllable on-premises cellular environment that supports up to 10,000 users in both static and mobile field conditions, communicating locally and connecting worldwide. By routing all cellular traffic to your […]
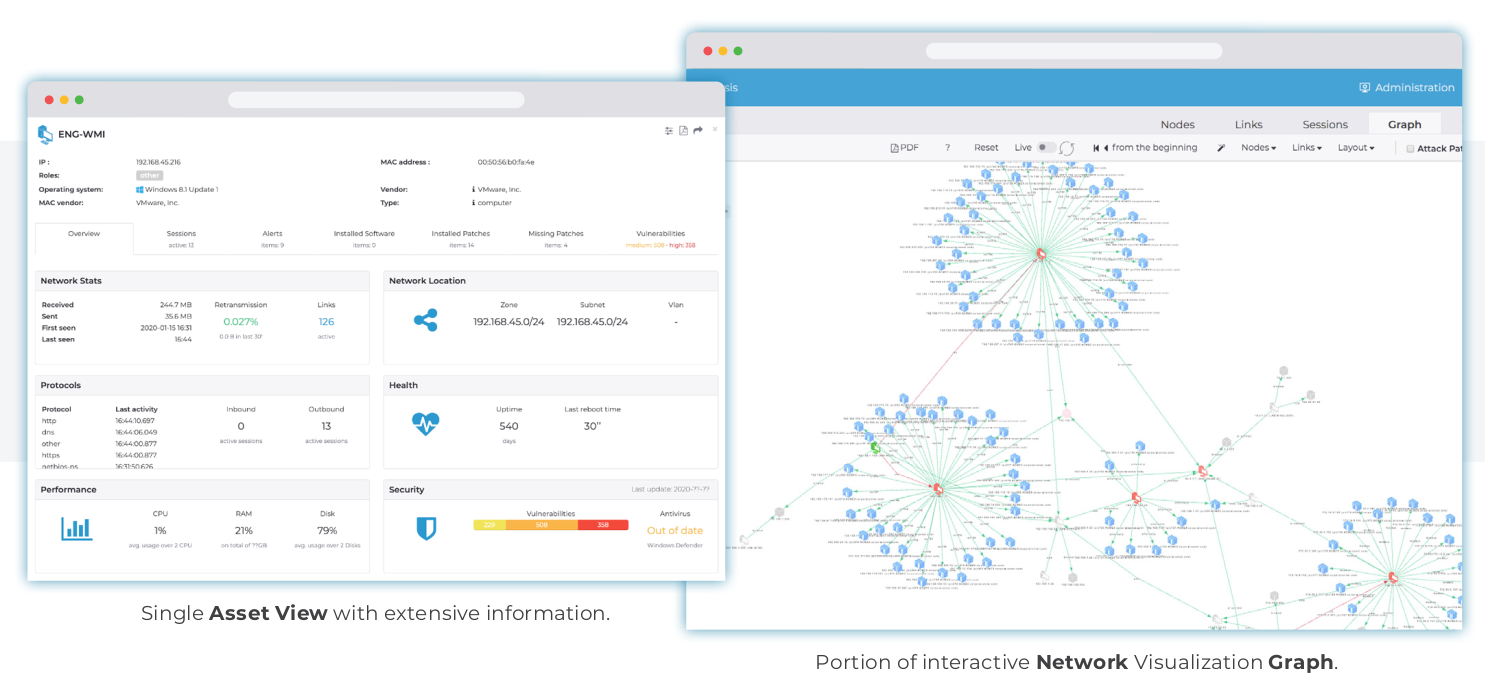
Better asset inventories and rapid threat detection should be sufficient justification for industrial companies to invest in continuous OT network monitoring. But product assessments should also consider future developments such as IT/OT cybersecurity convergence, external security support and digital transformation. Continuous operational technology (OT) network monitoring has become an essential part of every industrial/OT cybersecurity […]